eScore
paloaltonetworks.comThe eScore is a comprehensive evaluation of a business's online presence and effectiveness. It analyzes multiple factors including digital presence, brand communication, conversion optimization, and competitive advantage.
Palo Alto Networks demonstrates exceptional digital presence through its high domain authority and world-renowned thought leadership from the Unit 42 threat intelligence group. Its content strategy is robust, effectively aligning with the search intent of both C-suite executives and technical practitioners across the globe. The company maintains a consistent and authoritative presence across multiple channels, leveraging its deep industry research to solidify its position as a primary source of cybersecurity intelligence.
The Unit 42 threat intelligence arm functions as a powerful, high-authority content engine, establishing the company not just as a vendor but as a foundational source of industry intelligence that drives high-value organic traffic.
Develop more interactive, top-of-funnel content like AI readiness assessments or industry-specific risk calculators to engage a broader audience earlier in the customer journey and improve lead capture.
The company's messaging is highly disciplined, consistently reinforcing the core strategic pillars of 'Platformization' and 'AI-powered security' across all digital assets. Communication is expertly tailored to different audiences, addressing the strategic concerns of CISOs and the technical pain points of security engineers with precision. They effectively use emotional appeals, such as FUD (Fear, Uncertainty, and Doubt) balanced with empowerment, to create urgency and present their platform as the definitive solution.
Excellent problem/solution framing that positions the rise of AI-driven attacks against their AI-powered platform, creating a compelling and timely narrative that resonates with the market.
The messaging assumes a high degree of technical sophistication. Creating a dedicated 'C-Suite Briefing' content hub that translates platform capabilities into financial ROI and business risk metrics would make the value proposition more accessible to economic buyers.
The website provides a logical and clear user flow for its target audience of knowledgeable professionals, guiding them effectively from thought leadership content to specific platform solutions. However, the analysis identifies clear friction points, such as an inconsistent visual hierarchy for calls-to-action and a high cognitive load in dense mega-menus. The lack of a prominent accessibility statement is a notable oversight for a company of this stature, representing a missed opportunity and potential risk.
A well-structured information architecture that logically organizes a complex portfolio of products, services, and threat intelligence, catering effectively to expert users who know what they are looking for.
Establish and enforce a strict visual hierarchy for Call-to-Action (CTA) buttons. Differentiating primary, secondary, and tertiary CTAs with a consistent system of color and weight will better guide users toward key conversion goals.
Palo Alto Networks has built a fortress of credibility through an overwhelming display of trust signals and third-party validation. The website prominently features its leadership positions in numerous Gartner and Forrester reports, extensive government and industry certifications (like FedRAMP and ISO), and a customer list that includes 95% of the Fortune 100. This is powerfully supplemented by transparent legal policies and compelling customer success evidence, leaving little room for doubt in the buyer's mind.
The extensive and easily accessible list of critical industry and government certifications serves as a massive competitive advantage, immediately establishing trust and qualifying them for high-value enterprise and public sector contracts.
Proactively publish documentation detailing how the company's AI-powered solutions align with emerging AI-specific regulations and ethical guidelines (e.g., EU AI Act) to get ahead of future compliance questions.
The company's competitive moat is exceptionally strong and sustainable, built on the strategic foundation of 'platformization'. This integrated approach creates high switching costs and a unified defense that point-solution competitors cannot easily replicate. The recent $25 billion acquisition of CyberArk, a leader in identity security, fills the most significant gap in their portfolio, creating a category-defining platform for the AI era and a formidable barrier to competition.
The integrated, three-platform strategy, now fortified with market-leading Identity Security, creates a comprehensive and defensible moat that is extremely difficult for competitors to replicate.
Aggressively focus on the deep and seamless technical integration of the CyberArk portfolio into the Cortex and Strata platforms to fully realize the 'better together' value proposition and avoid the perception of a loosely-coupled suite.
Palo Alto Networks is built for scalable growth, demonstrated by its elite 'Rule-of-50' status, which reflects a world-class balance of strong growth and high profitability. The business model, with its increasing mix of high-margin recurring revenue, has massive operational leverage. Clear expansion vectors exist in penetrating the mid-market through MSSP channels and leveraging the CyberArk acquisition to drive immense cross-sell revenue into their vast enterprise customer base.
A highly efficient and profitable growth model, evidenced by achieving 'Rule-of-50' status for five consecutive years and generating strong free cash flow, which allows for reinvestment in R&D and strategic M&A.
Develop and execute a dedicated go-to-market strategy for the mid-market segment, including tailored product bundles and a higher-velocity sales motion, to unlock a significant new addressable market.
The business model exhibits outstanding coherence, with a clear and disciplined strategic focus on becoming the definitive cybersecurity platform. The pivot to a recurring revenue model has been highly successful, driving predictable growth in Next-Generation Security ARR. The transformative acquisition of CyberArk is a masterful move that aligns perfectly with market trends and demonstrates a strong ability to allocate capital to shape the market and fortify their long-term vision.
The company's 'platformization' strategy is a masterclass in business model coherence, directly addressing the market's primary pain point (vendor complexity) and creating a virtuous cycle of customer stickiness, increased wallet share, and higher lifetime value.
Simplify the complexity of the product portfolio and its associated licensing models. This would shorten enterprise sales cycles and make the platform's value proposition easier to consume for new customers and market segments.
As a market leader in multiple cybersecurity segments, Palo Alto Networks exerts significant market power. The company demonstrates strong pricing power, positioning itself as a premium solution and successfully commanding high margins. Its ability to make bold, market-shaping moves, such as the $25 billion CyberArk acquisition, shows a high degree of market influence. The company's vision for platformization is setting the strategic agenda for the entire industry.
The ability to define and lead the market narrative around strategic concepts like 'platformization' and 'identity-first security for the AI era', effectively forcing competitors to react to their strategic moves.
Develop a more direct competitive positioning against the bundled, 'good enough' security offerings from Microsoft. This requires clearly articulating the superior security efficacy and long-term TCO of a dedicated, best-in-class platform.
Business Overview
Business Classification
Platform-based Cybersecurity Solutions
Hybrid (Hardware, SaaS, Professional Services)
Cybersecurity
Sub Verticals
- •
Network Security
- •
Cloud Security
- •
Security Operations (SecOps)
- •
Endpoint Security
- •
Identity Security (post-CyberArk acquisition)
Mature
Maturity Indicators
- •
Consistent double-digit revenue growth ($9.2B in FY2025).
- •
Established global market leader in multiple cybersecurity segments.
- •
Large-scale strategic acquisitions, such as the $25B deal for CyberArk.
- •
Strong recurring revenue base (Next-Generation Security ARR of $5.6B).
- •
Serving 95% of the Fortune 100.
Enterprise
Steady
Revenue Model
Primary Revenue Streams
- Stream Name:
Subscriptions
Description:Recurring revenue from cloud-delivered security services, threat prevention, URL filtering, endpoint protection (Cortex), and cloud security (Prisma). This is the largest and fastest-growing revenue component.
Estimated Importance:Primary
Customer Segment:Large Enterprise, Government, Service Providers
Estimated Margin:High
- Stream Name:
Product (Hardware & Software)
Description:Sale of physical and virtual next-generation firewall appliances (Strata platform) and associated software licenses.
Estimated Importance:Secondary
Customer Segment:Large Enterprise, Government, Service Providers
Estimated Margin:Medium
- Stream Name:
Support and Professional Services
Description:Maintenance contracts for hardware/software products and high-value consulting services from the Unit 42 team, including incident response, proactive assessments, and strategic advisory.
Estimated Importance:Tertiary
Customer Segment:Large Enterprise, Government
Estimated Margin:Medium
Recurring Revenue Components
- •
SaaS subscriptions for Prisma (Cloud Security) and Cortex (SecOps) platforms
- •
Threat prevention and intelligence subscriptions
- •
Annual support and maintenance contracts
- •
Managed Detection and Response (MDR) services
Pricing Strategy
Enterprise Subscription & Tiered Licensing
Premium
Opaque
Pricing Psychology
- •
Bundling (Platformization Strategy)
- •
Tiered Pricing (based on features and support levels)
- •
Value-Based Pricing (tied to security outcomes and risk reduction)
Monetization Assessment
Strengths
- •
Strong shift to high-margin, predictable recurring revenue from subscriptions.
- •
High customer lifetime value (LTV) due to significant switching costs.
- •
Platformization strategy encourages larger deal sizes and cross-selling across the three main platforms (Strata, Prisma, Cortex).
Weaknesses
- •
Premium pricing may be a barrier for smaller to mid-sized enterprises.
- •
Complexity of product portfolio and pricing can create a long sales cycle.
- •
Aggressive bundling and discounting to drive platform adoption could temporarily impact margins.
Opportunities
- •
Monetize integrated Identity Security solutions following the CyberArk acquisition, creating a new multi-billion dollar revenue pillar.
- •
Expand AI-driven security services (Precision AI®) as a premium offering.
- •
Develop consumption-based pricing models for cloud security services to attract cloud-native businesses.
Threats
- •
Intense price competition from rivals like Fortinet.
- •
Customer budget constraints in a challenging macroeconomic environment could lead to pressure for discounts.
- •
Emergence of 'good enough' security solutions from infrastructure vendors (e.g., cloud providers) could challenge premium positioning.
Market Positioning
Integrated Security Platform Leader
Leader in key segments like Network Firewalls, but faces intense competition across the broader cybersecurity landscape from specialists like CrowdStrike and Zscaler, and platform players like Fortinet.
Target Segments
- Segment Name:
Large Enterprise C-Suite (CISO, CIO, CEO)
Description:Decision-makers in Fortune 1000 or equivalent global organizations responsible for overall business risk, digital transformation, and cybersecurity strategy.
Demographic Factors
- •
Global or multinational operations
- •
High revenue ($1B+)
- •
Complex, hybrid IT environments (on-prem, multi-cloud)
Psychographic Factors
- •
Risk-averse, focused on compliance and brand protection
- •
Seeking strategic partners, not just vendors
- •
Value vendor consolidation to reduce complexity and improve efficiency
Behavioral Factors
- •
Influenced by industry analyst reports (e.g., Gartner, Forrester)
- •
Engage in long, relationship-based sales cycles
- •
High investment in digital transformation and AI initiatives
Pain Points
- •
Vendor sprawl and tool fatigue
- •
Difficulty integrating disparate security solutions
- •
Shortage of skilled cybersecurity talent
- •
Pressure to demonstrate ROI on security spending to the board
Fit Assessment:Excellent
Segment Potential:High
- Segment Name:
Security Operations (SecOps) & Cloud Architects
Description:Technical practitioners responsible for day-to-day security monitoring, threat response, and securing cloud-native applications and infrastructure.
Demographic Factors
Mid-to-senior level technical roles
Work in Security Operations Centers (SOCs) or cloud engineering teams
Psychographic Factors
- •
Detail-oriented and results-driven
- •
Value efficiency, automation, and technical superiority
- •
Seek to reduce alert fatigue and Mean Time to Respond (MTTR)
Behavioral Factors
- •
Active in technical communities and forums
- •
Require hands-on demos and proof-of-concept trials
- •
Prioritize product integration and API accessibility
Pain Points
- •
Overwhelmed by high volume of security alerts
- •
Lack of visibility across hybrid and multi-cloud environments
- •
Manual, repetitive tasks slowing down incident response
- •
Struggling to secure the full application lifecycle ('code to cloud')
Fit Assessment:Excellent
Segment Potential:High
Market Differentiation
- Factor:
Integrated, Three-Platform Strategy
Strength:Strong
Sustainability:Sustainable
- Factor:
AI-Driven Security (Precision AI®)
Strength:Moderate
Sustainability:Temporary
- Factor:
Unit 42 Threat Intelligence & Consulting
Strength:Strong
Sustainability:Sustainable
- Factor:
Massive Enterprise Customer Base
Strength:Strong
Sustainability:Sustainable
Value Proposition
To be the cybersecurity partner of choice by providing an end-to-end, AI-powered security platform that simplifies complexity and proactively prevents threats across the network, cloud, and enterprise.
Good
Key Benefits
- Benefit:
Reduced Complexity through Platformization
Importance:Critical
Differentiation:Somewhat unique
Proof Elements
Three integrated platforms: Strata, Prisma, Cortex
Customer testimonials on vendor consolidation
- Benefit:
Proactive Threat Prevention with AI
Importance:Critical
Differentiation:Somewhat unique
Proof Elements
- •
Metrics on 'inline attacks blocked per day'
- •
Promotion of 'Precision AI'
- •
Leadership in Gartner Magic Quadrants for security products
- Benefit:
Comprehensive Visibility and Control
Importance:Important
Differentiation:Common
Proof Elements
Coverage for network, cloud, IoT, and endpoints
Acquisition of CyberArk to add Identity Security
Unique Selling Points
- Usp:
The strategic vision of 'platformization' to consolidate the fragmented cybersecurity market into a single, integrated architecture.
Sustainability:Long-term
Defensibility:Strong
- Usp:
Integration of world-class Unit 42 threat intelligence directly into the product ecosystem and as a standalone elite consulting service.
Sustainability:Long-term
Defensibility:Strong
- Usp:
The pending acquisition of CyberArk, creating a unique platform that deeply integrates identity security with network, cloud, and SOC operations.
Sustainability:Long-term
Defensibility:Strong
Customer Problems Solved
- Problem:
Managing a portfolio of dozens of non-integrated security point solutions.
Severity:Critical
Solution Effectiveness:Complete
- Problem:
Inability to detect and respond to sophisticated, multi-vector cyberattacks in real-time.
Severity:Critical
Solution Effectiveness:Partial
- Problem:
Lack of security expertise and resources to manage a modern security program.
Severity:Major
Solution Effectiveness:Partial
Value Alignment Assessment
High
The business model directly addresses the primary market trends of vendor consolidation, the need for AI-driven security, Zero Trust architecture, and securing cloud environments.
High
The value proposition strongly resonates with the core pain points of CISOs (complexity, risk) and technical practitioners (alert fatigue, lack of visibility).
Strategic Assessment
Business Model Canvas
Key Partners
- •
Major Cloud Providers (AWS, Google Cloud, Microsoft Azure)
- •
Global System Integrators and Resellers (Channel Partners)
- •
Technology Alliance Partners (e.g., Splunk, ServiceNow)
- •
Cyber Insurance Providers and Law Firms (via Unit 42)
Key Activities
- •
Research & Development in AI and cybersecurity
- •
Strategic Mergers & Acquisitions
- •
Global Sales & Marketing to enterprise clients
- •
Threat Intelligence Research (Unit 42)
- •
Platform Integration Engineering
Key Resources
- •
Extensive patent portfolio and proprietary technology
- •
Elite cybersecurity talent (researchers, engineers, incident responders)
- •
Strong brand reputation and market leadership
- •
Large, high-value enterprise customer base
Cost Structure
- •
High R&D investment
- •
Significant Sales & Marketing expenses for enterprise sales
- •
Cost of revenue for hardware and cloud infrastructure
- •
Capital allocation for M&A activities
Swot Analysis
Strengths
- •
Market leadership and strong brand recognition.
- •
Comprehensive, integrated platform approach is a key differentiator.
- •
Large and loyal enterprise customer base with high switching costs.
- •
Strong financial performance with growing recurring revenue.
- •
World-class threat intelligence from Unit 42.
Weaknesses
- •
Premium pricing can be a barrier to entry for smaller organizations.
- •
Potential for integration challenges and product bloat from numerous acquisitions.
- •
Perception of complexity in deploying and managing the full platform.
- •
Growth is slowing from previous hyper-growth phases.
Opportunities
- •
Massive cross-selling and up-selling opportunity with the CyberArk customer base.
- •
Capitalize on the growing need for securing AI workloads and infrastructure.
- •
Further penetration into the cloud security (CNAPP) and SASE markets.
- •
Expand managed service offerings to address the cybersecurity skills gap.
Threats
- •
Intense competition from both best-of-breed point solutions (e.g., CrowdStrike, Zscaler) and other platform vendors (e.g., Fortinet, Cisco).
- •
Rapidly evolving threat landscape requiring continuous high R&D investment.
- •
Potential for disruption from cloud providers embedding more security features into their core platforms.
- •
Execution risk in integrating a large acquisition like CyberArk successfully.
Recommendations
Priority Improvements
- Area:
Post-Acquisition Integration
Recommendation:Develop and clearly articulate a 12-18 month roadmap for the technical and go-to-market integration of CyberArk's identity security platform into the Prisma and Cortex ecosystems to realize synergy value and reassure customers.
Expected Impact:High
- Area:
Market Segmentation Strategy
Recommendation:Create bundled offerings and potentially a streamlined pricing model tailored for the upper mid-market to expand the total addressable market without diluting the premium enterprise brand.
Expected Impact:Medium
- Area:
Product Marketing & Messaging
Recommendation:Simplify the 'platformization' message to focus on specific, quantifiable business outcomes (e.g., cost reduction, MTTR improvement, risk score reduction) to better resonate with executive and board-level stakeholders.
Expected Impact:Medium
Business Model Innovation
- •
Launch a strategic investment arm (Corporate Venture Capital) to invest in early-stage AI security startups, creating an ecosystem and future acquisition pipeline.
- •
Develop a consumption-based 'security-as-code' model where developers can programmatically consume security services via API, aligning with modern DevOps workflows.
- •
Explore offering integrated cyber insurance products underwritten by partners, leveraging Palo Alto's security posture data for dynamic risk assessment.
Revenue Diversification
- •
Expand Unit 42's strategic advisory services to include CISO-as-a-Service and virtual SOC offerings for companies that cannot afford full-time teams.
- •
Develop and monetize advanced cybersecurity training and certification programs beyond product-specific training, creating a new education-based revenue stream.
- •
Monetize anonymized threat intelligence data streams for financial services and government clients for advanced risk modeling.
Palo Alto Networks is successfully executing a strategic business model evolution from a best-in-class firewall provider to a dominant, integrated cybersecurity platform. The core strategy of 'platformization'—consolidating security functions into three main pillars (Strata, Prisma, Cortex)—is a direct and effective response to the primary pain point of its target enterprise market: vendor complexity. This move increases customer stickiness, raises switching costs, and drives larger, more strategic deals.
The company's growth trajectory is sustained by a savvy blend of organic R&D, particularly in AI, and aggressive, strategic acquisitions. The announced acquisition of CyberArk is a masterstroke that catapults them into a leadership position in the critical Identity Security market, a necessary pillar for any true end-to-end security platform and Zero Trust architecture. This is not merely a product extension but a fundamental business model expansion that will create significant cross-sell synergies and a more defensible competitive moat.
Financially, the model is shifting favorably towards high-margin, predictable subscription and recurring revenue, which is well-received by investors. The primary challenges are execution risks associated with integrating large acquisitions like CyberArk, managing the inherent complexity of a vast portfolio, and fending off nimble, best-of-breed competitors in high-growth segments like cloud and endpoint security. Future success will depend on their ability to seamlessly integrate acquired technologies, simplify their go-to-market messaging around tangible business outcomes, and continue to innovate at the pace of the rapidly evolving AI-driven threat landscape.
Competitors
Competitive Landscape
Mature
Moderately concentrated
Barriers To Entry
- Barrier:
High Research & Development Costs
Impact:High
- Barrier:
Brand Reputation and Trust
Impact:High
- Barrier:
Extensive Threat Intelligence Data
Impact:High
- Barrier:
High Customer Switching Costs
Impact:Medium
- Barrier:
Complex Regulatory Compliance
Impact:Medium
- Barrier:
Established Sales Channels and Partnerships
Impact:High
Industry Trends
- Trend:
Platform Consolidation ('Platformization')
Impact On Business:Reinforces Palo Alto Networks' core strategy of offering an integrated, end-to-end security platform, increasing customer stickiness and wallet share.
Timeline:Immediate
- Trend:
AI-Driven Threats and Defenses
Impact On Business:Central to Palo Alto's messaging ('Precision AI'). Creates an arms race where superior AI/ML models for threat detection become a key differentiator.
Timeline:Immediate
- Trend:
Convergence of Networking and Security (SASE)
Impact On Business:Puts Palo Alto's Prisma SASE in direct competition with networking giants like Cisco and cloud-native specialists like Zscaler.
Timeline:Immediate
- Trend:
Identity as the New Security Perimeter
Impact On Business:Validates the strategic, high-value acquisition of CyberArk, positioning Palo Alto Networks to lead in identity-aware security architectures.
Timeline:Immediate
- Trend:
Shift-Left and Cloud-Native Security (DevSecOps)
Impact On Business:Increases demand for Prisma Cloud's capabilities in securing workloads from code to cloud, competing with cloud-native startups and CSP native tools.
Timeline:Near-term
Direct Competitors
- →
Fortinet
Market Share Estimate:Leader in NGFW/UTM unit shipments (over 50% market share in firewall adoption by some metrics), strong contender in SASE and XDR.
Target Audience Overlap:High
Competitive Positioning:Price/performance leader, offering a broad, integrated 'Security Fabric' architecture, particularly strong in SMB, mid-market, and distributed enterprise.
Strengths
- •
Strong price-to-performance ratio and lower Total Cost of Ownership (TCO).
- •
Broad, integrated product portfolio (Security Fabric) covering network, endpoint, and cloud.
- •
High-performance hardware powered by custom ASICs (NP7, CP9).
- •
Strong foothold in the SD-WAN market.
- •
Often praised for ease of deployment and management.
Weaknesses
- •
Perceived as less innovative in advanced, AI-driven threat detection compared to Palo Alto.
- •
SASE offering is considered less mature and not as natively cloud-delivered.
- •
Less established brand reputation in the high-end, large enterprise segment compared to Palo Alto.
- •
Performance can degrade significantly when all security services are enabled.
Differentiators
- •
Custom ASIC hardware for accelerated performance.
- •
Integrated 'Security Fabric' approach from a single OS (FortiOS).
- •
Strong value proposition for price-sensitive customers.
- →
Cisco
Market Share Estimate:Major player across networking and security; a top vendor in SASE and leader in SD-WAN.
Target Audience Overlap:High
Competitive Positioning:Leverages its massive networking install base to cross-sell a broad security portfolio, positioning itself as an end-to-end enterprise IT and security provider.
Strengths
- •
Dominant position in enterprise networking provides a massive customer base for cross-selling.
- •
Comprehensive security portfolio covering network, endpoint, cloud, and now SIEM/observability with Splunk acquisition.
- •
Strong brand trust and established enterprise relationships.
- •
Robust SASE offering combining Meraki SD-WAN and Umbrella SSE.
- •
Significant investment in AI across its portfolio.
Weaknesses
- •
Portfolio can feel less integrated due to being built on numerous acquisitions (Sourcefire, Duo, Splunk).
- •
Security products can be complex to manage, especially in non-Cisco environments.
- •
Sometimes perceived as a 'networking company first, security second'.
- •
Licensing can be complex and confusing for customers.
Differentiators
- •
Deep integration with its own market-leading networking hardware.
- •
End-to-end visibility from the network to the application layer.
- •
Massive threat intelligence from Talos research group.
- →
CrowdStrike
Market Share Estimate:A market leader in Endpoint Protection (EPP), Endpoint Detection and Response (EDR), and XDR.
Target Audience Overlap:Medium-High
Competitive Positioning:A cloud-native security pioneer focused on stopping breaches via its Falcon platform, emphasizing endpoint and identity protection with elite threat intelligence.
Strengths
- •
Market-leading EDR/XDR solution (Falcon platform).
- •
Lightweight, single-agent cloud-native architecture.
- •
Superior threat intelligence and human-led threat hunting (Falcon OverWatch).
- •
Strong brand reputation for security efficacy and innovation.
- •
Excellent user interface and ease of use are often cited.
Weaknesses
- •
Less established in network and cloud security (CNAPP), though rapidly expanding.
- •
Portfolio is narrower than Palo Alto's, not a direct competitor in the firewall/SASE space.
- •
Can be a premium-priced solution in the endpoint market.
- •
Lacks some advanced features like remote wipe capabilities.
Differentiators
- •
Cloud-native from the ground up.
- •
Focus on 'stopping the breach' rather than just blocking malware.
- •
Combination of AI/ML with elite human threat hunters.
- →
Zscaler
Market Share Estimate:Market share leader in the Security Service Edge (SSE) and overall SASE market by revenue.
Target Audience Overlap:Medium-High
Competitive Positioning:Cloud-native Zero Trust security leader, providing secure access to the internet and private applications without a traditional network perimeter.
Strengths
- •
True cloud-native, multi-tenant proxy architecture built for scalability and performance.
- •
Market leader and pioneer in Zero Trust network access (ZTNA).
- •
Strong performance in SSL/TLS inspection at scale.
- •
Often praised for ease of use and centralized policy management.
- •
Proven ability to reduce lateral threat movement by connecting users to apps, not the network.
Weaknesses
- •
Narrower product focus than Palo Alto; primarily focused on SSE and ZTNA.
- •
Does not offer NGFW or comprehensive endpoint security solutions.
- •
Relies on partners for the SD-WAN component of SASE.
- •
Legacy firewall vendors like Palo Alto are catching up with their own integrated SASE platforms.
Differentiators
- •
Proxy-based architecture versus firewall-based approach.
- •
Connects users and devices to applications, not the corporate network.
- •
Over a decade of experience as a cloud-native security provider.
- →
Check Point Software
Market Share Estimate:A foundational leader in the firewall market, remains a top 4 player in network security.
Target Audience Overlap:High
Competitive Positioning:Positions itself as a comprehensive, prevention-first security provider with its 'Infinity' architecture, leveraging strong R&D and a legacy of security expertise.
Strengths
- •
Strong reputation for security effectiveness and threat prevention.
- •
Unified management console (SmartConsole) is often praised for its power and usability.
- •
Comprehensive product portfolio covering network, cloud, endpoint, and mobile.
- •
Strong R&D capabilities and a long history in the market.
Weaknesses
- •
Perceived as slower to innovate, particularly in cloud-native and SASE offerings.
- •
Can be seen as a more traditional, legacy security vendor.
- •
Market share has been challenged by more aggressive competitors like Palo Alto and Fortinet.
- •
Complex licensing with extra costs for many features.
Differentiators
- •
Emphasis on a 'prevention-first' security philosophy.
- •
Infinity Architecture aims for a consolidated security experience.
- •
Strong focus on threat intelligence from Check Point Research.
Indirect Competitors
- →
Microsoft
Description:Microsoft has become a cybersecurity titan by bundling a comprehensive suite of security tools (Defender, Sentinel, Entra ID) into its popular enterprise software licenses (e.g., E5). This makes its security offerings a cost-effective and highly integrated choice for organizations already in the Microsoft ecosystem.
Threat Level:High
Potential For Direct Competition:Already a direct competitor in many areas (XDR, Identity, Cloud Security) and expanding rapidly. Their ability to bundle security at a low marginal cost is a major disruptive threat.
- →
Cloud Service Providers (AWS, Google Cloud)
Description:Major cloud providers offer an increasingly sophisticated set of native security tools for their platforms (e.g., AWS GuardDuty, GCP Security Command Center). These tools are perfectly integrated and easy to deploy for customers heavily invested in a single cloud.
Threat Level:Medium
Potential For Direct Competition:For single-cloud customers, native tools can reduce the need for third-party CNAPP solutions like Prisma Cloud. However, multi-cloud complexity remains a key value proposition for Palo Alto.
- →
Okta
Description:A market leader in Identity and Access Management (IAM), providing single sign-on, multi-factor authentication, and user lifecycle management. While often a partner, the line between identity and security is blurring.
Threat Level:Medium
Potential For Direct Competition:Palo Alto's acquisition of CyberArk turns the identity space into a direct competitive battleground. Okta is now a primary competitor in the race to define identity-led security.
Competitive Advantage Analysis
Sustainable Advantages
- Advantage:
Integrated Security Platform
Sustainability Assessment:The 'platformization' strategy creates high switching costs and operational dependency, making the advantage highly sustainable as long as integration remains best-in-class.
Competitor Replication Difficulty:Hard
- Advantage:
Brand Reputation and Enterprise Trust
Sustainability Assessment:Palo Alto Networks is widely regarded as a premium, top-tier security vendor, a reputation built over years that is difficult for competitors to erode quickly.
Competitor Replication Difficulty:Hard
- Advantage:
Unit 42 Threat Intelligence
Sustainability Assessment:The vast amount of threat data collected across its platform and the expertise of its research team create a powerful data and intelligence moat that is difficult to replicate.
Competitor Replication Difficulty:Hard
- Advantage:
Large and Loyal Enterprise Customer Base
Sustainability Assessment:Deeply embedded in the infrastructure of the world's largest companies, providing a stable revenue base and significant cross-sell/upsell opportunities.
Competitor Replication Difficulty:Hard
Temporary Advantages
{'advantage': 'Leadership in Analyst Reports (Gartner, Forrester)', 'estimated_duration': '1-2 years'}
{'advantage': 'First-mover advantage on specific AI-powered features', 'estimated_duration': '12-18 months'}
Disadvantages
- Disadvantage:
High Cost / Premium Pricing
Impact:Major
Addressability:Difficult
- Disadvantage:
Product and Platform Complexity
Impact:Major
Addressability:Moderately
- Disadvantage:
Integration Challenges from Acquisitions
Impact:Minor
Addressability:Moderately
Strategic Recommendations
Quick Wins
- Recommendation:
Aggressively market the integrated Palo Alto + CyberArk vision, focusing on securing both human and machine identities in the AI era to capitalize on the acquisition announcement.
Expected Impact:High
Implementation Difficulty:Easy
- Recommendation:
Launch targeted 'competitive displacement' campaigns focusing on the performance degradation of competitors like Fortinet when full security services are enabled.
Expected Impact:Medium
Implementation Difficulty:Moderate
- Recommendation:
Create bundled 'Platformization Starter Kits' for existing customers to accelerate adoption of adjacent products (e.g., Strata customers adopting Cortex).
Expected Impact:High
Implementation Difficulty:Moderate
Medium Term Strategies
- Recommendation:
Deepen the technical integration between Strata, Prisma, Cortex, and now CyberArk, focusing on a unified data model and single-pane-of-glass management to deliver on the platform promise.
Expected Impact:High
Implementation Difficulty:Difficult
- Recommendation:
Develop a simplified, mid-market offering to more effectively compete with Fortinet's price/performance advantage in that segment.
Expected Impact:High
Implementation Difficulty:Difficult
- Recommendation:
Intensify competition with Microsoft by highlighting the security risks of vendor monoculture and showcasing superior efficacy from a dedicated, best-in-class security platform.
Expected Impact:Medium
Implementation Difficulty:Moderate
Long Term Strategies
- Recommendation:
Establish the industry standard for securing AI development and deployment pipelines, moving beyond securing AI usage to securing AI creation.
Expected Impact:High
Implementation Difficulty:Difficult
- Recommendation:
Expand into adjacent markets like Operational Technology (OT) and Industrial Control Systems (ICS) security, leveraging existing network security expertise.
Expected Impact:Medium
Implementation Difficulty:Difficult
- Recommendation:
Build out a developer-first ecosystem around Prisma Cloud to make it the default security tool for cloud-native developers, embedding security directly into the CI/CD pipeline.
Expected Impact:High
Implementation Difficulty:Difficult
Solidify the position as the undisputed premium, end-to-end security platform for the AI-native enterprise. Shift messaging from 'cybersecurity provider' to 'digital immune system' for complex, multi-cloud organizations where security efficacy is non-negotiable.
Differentiate on three core pillars: 1) The quality and real-time nature of AI-driven prevention, 2) The seamless integration of a truly comprehensive platform (Network, Cloud, SOC, and Identity), and 3) The elite, human-led expertise of Unit 42 threat intelligence and incident response.
Whitespace Opportunities
- Opportunity:
Cybersecurity for Small and Medium-sized Businesses (SMBs)
Competitive Gap:Palo Alto is primarily enterprise-focused, leaving a large, price-sensitive SMB market dominated by competitors like Fortinet. A tailored, simplified, and channel-friendly offering could capture significant share.
Feasibility:Medium
Potential Impact:High
- Opportunity:
Deepening DevSecOps Integration
Competitive Gap:While Prisma Cloud is strong, there is a gap for a solution that is truly beloved by developers. Winning the developer workflow means winning the future of cloud security.
Feasibility:Medium
Potential Impact:High
- Opportunity:
Cyber Insurance Partnerships and Validation
Competitive Gap:No vendor has successfully created a clear link between platform adoption and reduced cyber insurance premiums. Formalizing this offers a powerful C-level value proposition.
Feasibility:Medium
Potential Impact:Medium
- Opportunity:
Managed Platform Services
Competitive Gap:Many enterprises lack the skills to manage a complex platform. Offering a premium, 'white glove' managed service for the entire Palo Alto platform could drive adoption and create a new high-margin revenue stream.
Feasibility:High
Potential Impact:High
Palo Alto Networks operates in a mature, intensely competitive, and rapidly evolving cybersecurity market. The dominant industry trend is 'platformization'—the consolidation of multiple point products into a single, integrated platform, a strategy Palo Alto Networks has championed. This approach is a direct response to customer fatigue from managing dozens of disparate security tools and is becoming the primary battleground for market leadership.
The company's direct competitive landscape is defined by a few key archetypes. Fortinet competes aggressively on price-to-performance, leveraging custom hardware to offer a compelling TCO, particularly in the mid-market. Cisco leverages its colossal networking footprint to bundle security solutions, posing a significant threat through its incumbency and recent strategic acquisitions like Splunk. In the modern, cloud-native arena, CrowdStrike dominates the endpoint (XDR) space with its lightweight agent and elite threat intelligence, while Zscaler leads the SASE/SSE market with its purpose-built proxy architecture for Zero Trust.
Palo Alto's key sustainable advantages are its premium brand reputation, its deeply integrated three-pillar platform (Strata, Prisma, Cortex), and the formidable threat intelligence of Unit 42. The recent, blockbuster agreement to acquire CyberArk is a masterstroke that addresses a critical gap and repositions the company at the forefront of the identity-centric security paradigm. This move directly counters the growing threat from identity specialists like Okta and the bundled identity offerings from Microsoft.
The most significant indirect threat comes from Microsoft. By bundling an increasingly capable security stack into its E5 licenses, Microsoft leverages its enterprise ubiquity to become the 'good enough' and cost-effective default for many organizations, representing a serious long-term disruptive force.
Strategic whitespace exists in the SMB market, deeper DevSecOps integration, and formalizing partnerships with the cyber insurance industry. Palo Alto's primary challenge will be to manage the complexity of its expanding platform and justify its premium pricing against lower-cost rivals and bundled offerings from hyperscalers. Future success hinges on flawlessly executing the CyberArk integration, continuing to lead in AI-driven security innovation, and proving that its integrated platform delivers superior security outcomes that justify the investment.
Messaging
Message Architecture
Key Messages
- Message:
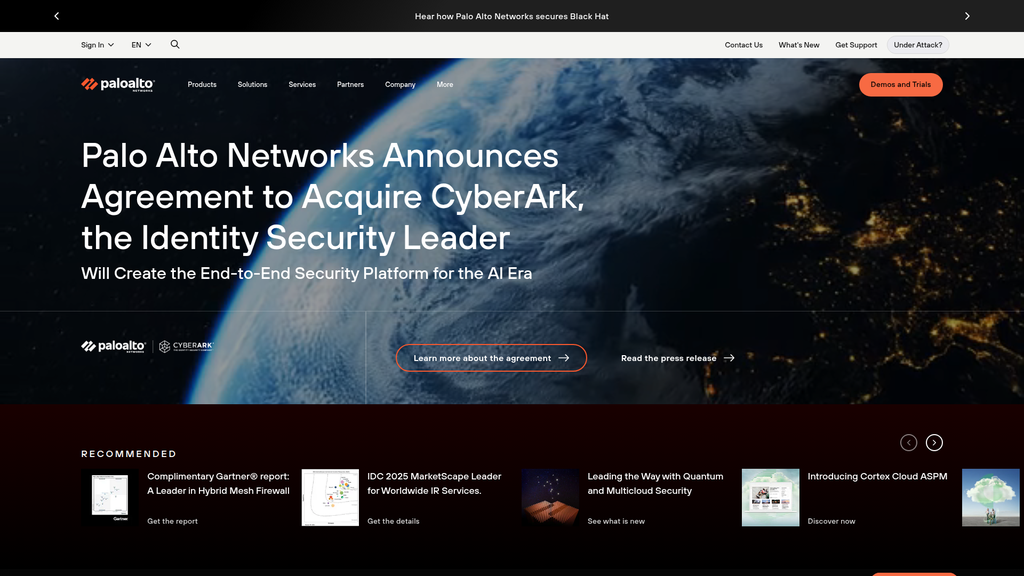
Palo Alto Networks is creating the End-to-End Security Platform for the AI Era, now including Identity Security through the acquisition of CyberArk.
Prominence:Primary
Clarity Score:High
Location:Homepage Hero Banner
- Message:
Platformization empowers you to harness AI-ready infrastructure and leverage services powered by Precision AI® to keep everything secure.
Prominence:Primary
Clarity Score:Medium
Location:Homepage - 'Why Palo Alto Networks' Section
- Message:
Our three core platforms—AI-Powered Network Security (Strata), AI-Driven Security Operations (Cortex), and Real-Time Cloud Security (Prisma)—provide comprehensive protection.
Prominence:Secondary
Clarity Score:High
Location:Homepage - Platforms Section
- Message:
Attackers are supercharging their speed and scale, creating an urgent need for a new, AI-driven approach to security.
Prominence:Secondary
Clarity Score:High
Location:Homepage - 'A new AI world is here' Section
- Message:
Our world-renowned threat intelligence (Unit 42) and incident response services provide an intelligence-driven, response-ready security posture.
Prominence:Tertiary
Clarity Score:High
Location:Homepage - Services Section & Cortex Research Page
The message hierarchy is logical and effective. It starts with a major strategic announcement (CyberArk acquisition) to frame the company's future direction. It then immediately addresses the core market challenge (AI threats) and presents the strategic solution ('Platformization'). This is followed by a clear breakdown of the three core platform pillars, providing tangible proof points. This structure successfully guides the user from high-level strategy to specific solution areas.
Messaging is highly consistent. The central themes of 'AI-powered', 'platform', and 'integration' are woven throughout the homepage, from the hero banner to the detailed product sections. The Cortex research page reinforces the company's expertise and authority, which is a core tenet of the main site's messaging. The use of branded terms like 'Precision AI®' and product family names (Strata, Prisma, Cortex) is uniform.
Brand Voice
Voice Attributes
- Attribute:
Authoritative
Strength:Strong
Examples
- •
Will Create the End-to-End Security Platform for the AI Era
- •
Platformization empowers you...
- •
Unit 42’s world-renowned threat researchers...
- •
Trusted by the best
- Attribute:
Innovative
Strength:Strong
Examples
- •
A new AI world is here
- •
powered by Precision AI®
- •
Here for you. Here for what’s next.
- •
Introducing the Platforms, powered by Precision AI
- Attribute:
Urgent
Strength:Moderate
Examples
- •
THE BAD NEWS: Attackers are supercharging their speed and scale.
- •
INCREASE IN RANSOMWARE ATTACKS (YoY, 2023)
- •
Under Attack? We’re Here.
- Attribute:
Technical
Strength:Moderate
Examples
- •
90% reduction in MTTR
- •
the only platform that merges the industry’s leading CNAPP with best-in-class CDR
- •
The Cortex research page is filled with technical reports on threat actors and malware.
Tone Analysis
Professional & Expert-Driven
Secondary Tones
Urgent & Cautionary
Empowering & Solution-Oriented
Tone Shifts
Shifts from high-level, C-suite strategic language in headlines to more technical, practitioner-focused language in platform descriptions.
The 'BAD NEWS' section adopts a cautionary, almost alarming tone, which then shifts to an empowering, confident tone in the 'WHY PALO ALTO NETWORKS' section.
Voice Consistency Rating
Excellent
Consistency Issues
No itemsValue Proposition Assessment
Palo Alto Networks provides the industry's most complete and AI-powered cybersecurity platform, consolidating network, cloud, and security operations to reduce complexity and proactively stop sophisticated threats at scale.
Value Proposition Components
- Component:
Platform Consolidation & Reduced Complexity
Clarity:Clear
Uniqueness:Somewhat Unique
Evidence
Platformization empowers you...
secure whatever, whenever, wherever — with less complexity.
- Component:
AI-Powered Threat Prevention
Clarity:Clear
Uniqueness:Somewhat Unique
Evidence
- •
powered by Precision AI®
- •
AI-Powered Network Security
- •
AI-Driven Security Operations
- Component:
Comprehensive, End-to-End Coverage
Clarity:Clear
Uniqueness:Unique
Evidence
Will Create the End-to-End Security Platform for the AI Era
Platforms for Network Security, Security Operations, and Cloud Security
- Component:
Elite Threat Intelligence & Services
Clarity:Clear
Uniqueness:Unique
Evidence
Unit 42’s world-renowned threat researchers...
Intelligence-driven. Response-ready.
Palo Alto Networks' primary differentiation is its strategic shift from a portfolio of products to a fully integrated, 'platformized' approach. While competitors offer solutions in specific areas (network, cloud, EDR), Palo Alto's messaging aggressively pushes the idea of a single, unified platform to solve enterprise-wide challenges. The recent CyberArk acquisition announcement powerfully reinforces this by adding a critical Identity Security pillar, aiming to create a category-of-one 'End-to-End Security Platform.' The branding of its threat intelligence arm, 'Unit 42,' also serves as a strong differentiator, positioning them not just as a vendor but as a leading research authority.
The messaging positions Palo Alto Networks as the market consolidator and visionary leader, moving beyond the feature-by-feature comparisons with point-solution competitors like CrowdStrike, Fortinet, or Zscaler. By focusing on 'platformization' for the 'AI Era,' they are attempting to define a new market category where they are the default choice for large enterprises seeking to simplify their security stack and improve efficacy. This positions them as a strategic partner to the C-suite, rather than just a technology provider.
Audience Messaging
Target Personas
- Persona:
C-Suite / Executives (CISO, CIO, CEO)
Tailored Messages
- •
Will Create the End-to-End Security Platform for the AI Era
- •
Drive innovation and digital transformation with AI.
- •
Platformization empowers you to harness AI-ready infrastructure.
- •
Securing Your AI-Powered Network Transformation: A Guide for C-Suite Leaders
Effectiveness:Effective
- Persona:
Security Practitioners / SOC Analysts / Engineers
Tailored Messages
- •
90% reduction in MTTR
- •
25x reduction in alerts & remediation workflows
- •
Explore Network Security
- •
Product Demo Center
- •
Cortex Cloud Security Research (Unit 42)
Effectiveness:Effective
- Persona:
Partners & Managed Service Providers
Tailored Messages
- •
Partner Portal
- •
Become a Partner
- •
Managed Services Program
- •
Tap into the world’s most interoperable cloud and AI security platform.
Effectiveness:Effective
Audience Pain Points Addressed
- •
Tool Sprawl & Complexity ('less complexity')
- •
Slow Threat Detection & Response ('90% reduction in MTTR')
- •
Sophisticated, AI-driven Attacks ('Attackers are supercharging their speed and scale')
- •
Alert Fatigue ('25x reduction in alerts')
- •
Inability to Secure New Technologies like GenAI ('A new AI world is here')
Audience Aspirations Addressed
- •
Enabling Secure Digital Transformation & Innovation
- •
Achieving a Proactive, Predictive Security Posture
- •
Consolidating Vendors to Improve Efficiency and Lower TCO
- •
Becoming Cyber Resilient
Persuasion Elements
Emotional Appeals
- Appeal Type:
Fear, Uncertainty, and Doubt (FUD)
Effectiveness:High
Examples
- •
The 'BAD NEWS' section with stark, rising statistics on zero-days, ransomware, and data breaches.
- •
Attackers are supercharging their speed and scale.
- •
Under Attack? We’re Here.
- Appeal Type:
Security & Empowerment
Effectiveness:High
Examples
- •
So you can defend at speed and scale.
- •
Platformization empowers you...
- •
Trusted by the best
- •
Secure whatever, whenever, wherever
Social Proof Elements
- Proof Type:
Industry Analyst Recognition
Impact:Strong
Examples
Prominent display of Gartner Magic Quadrant and Forrester Wave leader rankings (e.g., '11x network security leader').
- Proof Type:
Customer Adoption Metrics
Impact:Strong
Examples
95% of the Fortune 100
70K Customers
- Proof Type:
Customer Logos & Testimonials
Impact:Strong
Examples
The 'Trusted by the best' section.
An embedded customer video testimonial.
- Proof Type:
Large-Scale Operational Data
Impact:Strong
Examples
Live-updating dashboard showing '11.3 B Attacks Prevented Inline', '480 B Endpoints scanned daily', etc.
Trust Indicators
- •
Extensive, detailed threat research from Unit 42.
- •
Specific, quantifiable performance metrics (e.g., '30.9 B inline attacks blocked per day').
- •
Clear links to technical documentation, privacy statements, and legal notices.
- •
Named authors on research reports, showcasing individual expertise.
Scarcity Urgency Tactics
The primary urgency tactic is the framing of the rapidly evolving threat landscape ('Attackers are supercharging their speed and scale'), implying that inaction is a significant risk.
Calls To Action
Primary Ctas
- Text:
Learn more about the agreement
Location:Homepage Hero
Clarity:Clear
- Text:
See our platform approach
Location:Why Palo Alto Networks Section
Clarity:Clear
- Text:
Explore Network Security / SecOps / Cloud Security
Location:Platforms Section
Clarity:Clear
- Text:
Demos and trials
Location:Top Navigation Bar
Clarity:Clear
- Text:
Our experts are standing by
Location:Engage with Us Section
Clarity:Clear
CTA effectiveness is very high. The website uses a multi-layered CTA strategy that effectively caters to different user intents and personas. High-level CTAs like 'See our platform approach' target strategic decision-makers, while specific 'Explore...' CTAs guide users toward product-level information. The 'Engage with Us' section is a masterclass in audience segmentation, providing clear, distinct paths for executives, specialists, partners, and customers, ensuring each visitor has a relevant next step.
Messaging Gaps Analysis
Critical Gaps
The business value and Total Cost of Ownership (TCO) of adopting a platform approach versus best-of-breed point solutions is implied but not explicitly articulated with quantifiable data on the homepage.
While messaging is strong for large enterprises, there is a lack of clear messaging or entry points for mid-market or smaller enterprises who may feel the platform is too complex or expensive for their needs.
Contradiction Points
No itemsUnderdeveloped Areas
The integration story for the CyberArk acquisition is, understandably, still in its infancy. The message is about the future ('Will Create...'), but the specific benefits and integrated workflows are not yet detailed.
The human element of cybersecurity could be further developed. While customer testimonials exist, stories about the internal experts at Palo Alto Networks (beyond Unit 42) could help humanize the highly technical brand.
Messaging Quality
Strengths
- •
Excellent problem/solution framing (AI-driven attacks vs. AI-powered platform).
- •
Overwhelming and effective use of social proof (analysts, customer numbers, logos, data points) to build credibility.
- •
Clear, logical message hierarchy that guides users from strategy to specifics.
- •
Strong audience segmentation in content and calls-to-action.
Weaknesses
The sheer volume of products, services, and branded terms can be overwhelming for a first-time visitor not already familiar with the company.
The language assumes a high degree of technical sophistication, potentially alienating less technical business leaders who are key economic buyers.
Opportunities
- •
Develop an interactive assessment tool to help prospects identify which parts of the platform are most critical for their specific security gaps.
- •
Create a dedicated 'C-Suite Briefing' content hub that translates the platform's technical capabilities into clear business outcomes, risk reduction metrics, and financial ROI.
- •
Launch a messaging campaign that simplifies the 'Platformization' concept into a more accessible and memorable narrative.
Optimization Roadmap
Priority Improvements
- Area:
Value Proposition
Recommendation:Develop a clear, data-driven TCO/ROI calculator or a whitepaper that quantifies the financial benefits of platform consolidation versus managing multiple point solutions. Feature this prominently in the 'Why Palo Alto Networks?' section.
Expected Impact:High
- Area:
Audience Messaging
Recommendation:Create a dedicated 'Solutions for Your Business Size' section on the homepage to better guide Small, Mid-Sized, and Enterprise customers to relevant content and product bundles.
Expected Impact:Medium
- Area:
Message Clarity
Recommendation:Introduce a simplified, animated explainer video at the top of the homepage that visualizes the concept of 'Platformization' and how the three core platforms work together to stop a threat. This would make the core concept more accessible to non-technical audiences.
Expected Impact:High
Quick Wins
In the 'Trusted by the best' section, add a clickable link to a dedicated page featuring more detailed customer case studies filterable by industry and use case.
Re-label the 'Perspectives' section to something more benefit-oriented like 'C-Suite Strategy & Insights' to better attract executive attention.
Long Term Recommendations
Fully weave the Identity Security narrative from the CyberArk acquisition into the core platform messaging, updating diagrams and value propositions across Strata, Prisma, and Cortex to reflect this new, integrated capability.
Build out a thought leadership platform around 'Securing the AI-Native Enterprise,' moving beyond just defending against AI threats to enabling secure AI adoption, to capture the next wave of market interest.
Palo Alto Networks executes a world-class strategic messaging strategy that effectively positions it as the definitive leader in the enterprise cybersecurity market. The messaging architecture is built on a powerful and timely foundation: the dual rise of AI as both a threat and a solution. This creates a compelling narrative that frames their core strategy of 'Platformization' not as a choice, but as a necessity for survival and innovation.
The brand's voice is authoritative and expert-driven, reinforced at every turn by an overwhelming arsenal of social proof, including #1 rankings from top analysts, adoption by 95% of the Fortune 100, and a live dashboard of staggering security metrics. This approach is designed to eliminate risk from the buyer's decision-making process. The value proposition is clearly focused on solving the CISO's biggest challenges: the complexity of a multi-vendor security stack and the accelerating sophistication of threats. The recent announcement of the CyberArk acquisition is a masterstroke, allowing them to credibly claim the ultimate high ground with a message of an 'End-to-End Security Platform.'
The messaging is skillfully segmented for different audiences, with high-level strategic concepts for executives and deep technical proof points for practitioners. The calls-to-action are exceptionally well-crafted, providing clear and relevant pathways for every type of visitor. The primary weakness is a potential for message overload; the sheer breadth of the portfolio can be intimidating. Furthermore, the messaging is squarely aimed at the global enterprise, leaving a significant opportunity to develop a more tailored value proposition for the mid-market. To optimize, the company should focus on simplifying its core 'Platformization' narrative for non-technical buyers and more explicitly articulating the financial ROI of consolidation, which will be critical for securing budget in a competitive economic environment.
Growth Readiness
Growth Foundation
Product Market Fit
Strong
Evidence
- •
Market leadership with 95% of the Fortune 100 as customers.
- •
Consistent recognition as a leader in multiple Gartner Magic Quadrants and Forrester Waves for SASE, Network Firewalls, and SecOps platforms.
- •
Strong financial performance with fiscal year 2025 revenue growing 15% to $9.2 billion.
- •
High customer commitment indicated by a Remaining Performance Obligation (RPO) of $15.8 billion, up 24% year-over-year.
- •
Successful "platformization" strategy driving broader adoption of integrated solutions, with Next-Generation Security (NGS) ARR growing 32% to $5.6 billion.
Improvement Areas
- •
Simplify messaging and product bundling for the mid-market to accelerate penetration in a new customer segment.
- •
Enhance the user experience for the unified platform to reduce complexity arising from the integration of numerous acquired products.
- •
Clearly articulate the integrated value proposition of the CyberArk acquisition to existing customers to drive rapid cross-selling.
Market Dynamics
12-14% CAGR (Compound Annual Growth Rate) projected through 2032.
Mature
Market Trends
- Trend:
Platform Consolidation
Business Impact:Strong tailwind for Palo Alto Networks' core 'platformization' strategy as CISOs look to reduce vendor complexity and improve integration.
- Trend:
AI-Driven Threats and Defenses
Business Impact:Creates significant demand for the company's AI-powered platforms (Precision AI®, Cortex XSIAM) and reinforces its innovation narrative. The AI security market is projected to reach over $93 billion by 2030.
- Trend:
Shift to Zero Trust Architectures
Business Impact:Directly aligns with Palo Alto Networks' product philosophy and solutions, making it a key enabler for enterprises adopting this strategic security model.
- Trend:
Convergence of Networking and Security (SASE)
Business Impact:Positions Prisma SASE as a critical growth engine, addressing the needs of hybrid workforces and distributed enterprises.
- Trend:
Identity as the New Perimeter
Business Impact:The $25 billion acquisition of CyberArk strategically positions the company to lead in this critical, high-growth area, especially with the rise of AI agents.
Excellent. The confluence of rising AI-driven cyber threats, vendor consolidation, and the strategic imperative for Zero Trust creates a highly favorable market environment for a platform leader like Palo Alto Networks.
Business Model Scalability
High
High-margin software and subscription model with significant upfront investment in R&D and sales, leading to strong operating leverage as revenue scales.
Strong. Demonstrated by expanding operating margins to over 30% and achieving "Rule-of-50" status (Revenue Growth % + FCF Margin %), indicating a highly efficient growth model.
Scalability Constraints
- •
Dependence on a large, highly-skilled, and expensive direct sales force for enterprise deals.
- •
Complexity of integrating a vast portfolio of acquired technologies into three seamless platforms.
- •
Intense competition for top-tier cybersecurity and AI engineering talent.
Team Readiness
Proven. The executive team, led by Nikesh Arora, has successfully navigated a major strategic pivot to a platform-based model and executed large-scale, transformative acquisitions.
Scalable but Complex. Organized around three core platforms (Strata, Prisma, Cortex) which aligns with the go-to-market strategy, but requires significant cross-functional coordination, especially post-acquisition.
Key Capability Gaps
- •
Post-Merger Integration: A critical need for dedicated teams to ensure the seamless technical and cultural integration of CyberArk to realize synergy targets.
- •
Mid-Market Sales Motion: The current enterprise-focused sales model may need augmentation with a lower-touch, higher-velocity model to effectively capture the mid-market.
- •
Partner Enablement for NGS: Need to accelerate the training and incentivization of channel partners to sell newer, more complex platform solutions beyond traditional firewalls.
Growth Engine
Acquisition Channels
- Channel:
Direct Enterprise Sales
Effectiveness:High
Optimization Potential:Medium
Recommendation:Equip the sales team with specific playbooks for selling the newly integrated CyberArk identity security solutions to the existing customer base of 95% of the Fortune 100.
- Channel:
Channel Partners & Resellers
Effectiveness:High
Optimization Potential:High
Recommendation:Launch a global partner enablement initiative focused on certifying partners on the three core platforms and incentivizing multi-platform sales and deployments.
- Channel:
Content & Thought Leadership (Unit 42)
Effectiveness:High
Optimization Potential:Medium
Recommendation:Increase the output of research and best-practice guides specifically addressing the security of enterprise AI deployments, leveraging insights from the CyberArk acquisition.
- Channel:
Strategic Alliances (e.g., Cloud Providers)
Effectiveness:Medium
Optimization Potential:High
Recommendation:Deepen co-selling and technical integrations with major cloud providers (AWS, Azure, GCP) to make Prisma Cloud the de facto security platform for multi-cloud environments.
Customer Journey
Dominated by a high-touch, consultative sales process for enterprise clients, involving executive briefings, product demos, and proofs-of-concept. The website serves as a primary resource for thought leadership, product information, and initial contact.
Friction Points
- •
Portfolio Complexity: The sheer breadth of products can be overwhelming for prospective customers trying to understand the right solution bundle.
- •
Long Sales Cycles: Enterprise security deals often involve multiple stakeholders and lengthy evaluation periods, which is inherent to the market but still a friction point.
- •
Integration Concerns: Customers may have concerns about the complexity and cost of migrating from incumbent point solutions to a full platform.
Journey Enhancement Priorities
{'area': 'Interactive Solution Builder', 'recommendation': "Develop an online tool that allows prospective customers to input their challenges (e.g., 'secure hybrid workforce', 'protect cloud applications') and receive a recommended platform configuration and value proposition."}
{'area': 'Platform Migration Program', 'recommendation': "Create a formal 'Platformization Program' that offers customers financial incentives, professional services, and technical support to consolidate their security stack and migrate from competitor point products."}
Retention Mechanisms
- Mechanism:
Platform Stickiness
Effectiveness:High
Improvement Opportunity:Deepen integrations between the three core platforms and the newly acquired identity pillar to make the unified solution indispensable to a customer's security operations.
- Mechanism:
Subscription & Renewal Model
Effectiveness:High
Improvement Opportunity:Proactively engage customers with data-driven insights on their security posture improvements and ROI to justify renewals and price increases.
- Mechanism:
Expansion Revenue (Cross-sell/Up-sell)
Effectiveness:High
Improvement Opportunity:Launch targeted campaigns to sell CyberArk's identity security solutions into the massive installed base of network and cloud security customers.
Revenue Economics
Very Strong. Indicated by high gross margins (around 74%) and consistently strong free cash flow margins (projected 37-38%), which is a hallmark of a highly profitable software/subscription business model.
High (Not publicly disclosed, but implied by strong net retention, high RPO, and profitability). The platform model significantly increases LTV by creating high switching costs and multiple expansion revenue streams.
Excellent. The company consistently operates well above the 'Rule of 40', recently hitting 46.4 and being a 'Rule-of-50' company for five consecutive years, showcasing a world-class balance of growth and profitability.
Optimization Recommendations
- •
Focus sales efforts on multi-platform deals, which have a higher initial contract value and lead to greater long-term customer value.
- •
Leverage the channel to reduce the cost of acquisition for mid-market customers.
- •
Use AI-driven analytics to identify existing customers with the highest propensity to buy additional platform modules or identity solutions.
Scale Barriers
Technical Limitations
- Limitation:
Platform Integration Complexity
Impact:High
Solution Approach:Invest heavily in a unified data architecture and common API framework across all products to ensure a seamless 'single pane of glass' experience and avoid creating a 'franken-platform'.
- Limitation:
Keeping Pace with AI Threat Evolution
Impact:High
Solution Approach:Continue to invest heavily in R&D and threat intelligence (Unit 42), and consider acqui-hires of specialized AI security research teams to stay ahead of adversaries.
Operational Bottlenecks
- Bottleneck:
Post-Acquisition Integration of CyberArk
Growth Impact:Successful integration is critical for realizing the deal's strategic value; failure could lead to operational disruption and slow cross-selling.
Resolution Strategy:Establish a dedicated, executive-led Integration Management Office (IMO) with clear workstreams for product, sales, marketing, and support integration, with aggressive 90 and 180-day targets.
- Bottleneck:
Scaling Professional Services & Customer Success
Growth Impact:As platform deals become more complex, the demand for expert deployment and optimization services will increase, potentially becoming a bottleneck to customer value realization.
Resolution Strategy:Expand the certified services partner ecosystem and invest in scalable digital customer success resources and training platforms.
Market Penetration Challenges
- Challenge:
Intense Competition
Severity:Critical
Mitigation Strategy:Compete on the basis of a superior, integrated platform rather than on individual product features. Key competitors include Fortinet, CrowdStrike, Zscaler, and Cisco. Emphasize the TCO and security outcome benefits of consolidation.
- Challenge:
Market Perception of 'Vendor Lock-in'
Severity:Major
Mitigation Strategy:Counter this objection by highlighting open APIs, extensive partner integrations (700+), and adherence to industry standards to demonstrate ecosystem-friendliness.
- Challenge:
Sustaining Premium Pricing
Severity:Major
Mitigation Strategy:Continuously demonstrate superior security efficacy and ROI through customer case studies, third-party validation, and quantifiable metrics (e.g., reduction in MTTR, fewer security incidents).
Resource Limitations
Talent Gaps
- •
AI Security Specialists: Experts in securing AI models and infrastructure.
- •
Identity Security Integration Architects: Technical experts to merge CyberArk technology into the core platforms.
- •
Cloud Security Experts: Deep specialists in AWS, Azure, and GCP environments.
Low. The company generates substantial free cash flow, sufficient to fund organic growth initiatives. Future large-scale M&A may require additional capital.
Infrastructure Needs
Unified Cloud-based Management Plane: Continued investment to scale the Strata Cloud Manager to handle the entire integrated portfolio.
Global Cloud Infrastructure (PoPs): Continued expansion of the global network for Prisma SASE to ensure low-latency performance for all customers.
Growth Opportunities
Market Expansion
- Expansion Vector:
Mid-Market Segment Penetration
Potential Impact:High
Implementation Complexity:High
Recommended Approach:Develop a specific go-to-market strategy including product bundles tailored for mid-market needs, a higher-velocity sales motion, and deeper engagement with Managed Security Service Providers (MSSPs).
- Expansion Vector:
Geographic Expansion in Asia-Pacific
Potential Impact:High
Implementation Complexity:Medium
Recommended Approach:Invest in local sales and support infrastructure, tailor marketing to regional compliance and threat landscapes, and build out the regional channel partner network.
Product Opportunities
- Opportunity:
Unified Identity-Aware Security Platform
Market Demand Evidence:The $25B acquisition of CyberArk validates the critical need for integrated identity security, driven by the rise of AI and cloud adoption.
Strategic Fit:Perfect. Fills the most significant gap in the existing platform portfolio.
Development Recommendation:Prioritize deep, native integration of CyberArk's Privileged Access Management (PAM) into Cortex XSIAM and Prisma Cloud to enable identity-based threat detection and response.
- Opportunity:
Security for AI Development & Deployment
Market Demand Evidence:Enterprises are rapidly adopting AI but lack mature tools to secure the AI development lifecycle (AI-SPM) and protect models from new attack vectors.
Strategic Fit:Excellent. Extends the 'shift-left' security concept from cloud-native apps (CNAPP) to AI models, aligning with the Prisma Cloud value proposition.
Development Recommendation:Develop or acquire technology focused on AI model vulnerability scanning, adversarial attack detection, and governance for large language models (LLMs).
Channel Diversification
- Channel:
Managed Security Service Providers (MSSPs)
Fit Assessment:Excellent
Implementation Strategy:Create a dedicated MSSP program with multi-tenant management capabilities, consumption-based pricing, and co-marketing funds to enable partners to build services on top of the Palo Alto Networks platforms.
- Channel:
Cloud Marketplaces (AWS, Azure, GCP)
Fit Assessment:Excellent
Implementation Strategy:Streamline procurement and deployment by offering the full suite of software-based solutions (Prisma Cloud, VM-Series, etc.) through major cloud marketplaces with integrated billing.
Strategic Partnerships
- Partnership Type:
Major Systems Integrators (SIs)
Potential Partners
- •
Accenture
- •
Deloitte
- •
IBM Consulting
Expected Benefits:Drive large-scale enterprise security transformation projects by embedding Palo Alto Networks' platforms into the SIs' reference architectures and managed service offerings.
- Partnership Type:
AI Platform Providers
Potential Partners
- •
NVIDIA
- •
Databricks
- •
Snowflake
Expected Benefits:Develop joint solutions to secure AI workloads and data pipelines, making Palo Alto Networks the default security partner for the AI ecosystem.
Growth Strategy
North Star Metric
Platform Annual Recurring Revenue (Platform ARR)
This metric directly measures the success of the core 'platformization' strategy. It focuses on high-quality, recurring revenue from customers who are deeply invested in the ecosystem, reflecting both new customer acquisition and successful cross-selling.
Increase the percentage of total ARR coming from customers with 3+ platform modules by 20% annually.
Growth Model
Hybrid: Enterprise Sales-Led & Platform-Expansion
Key Drivers
- •
Land & Expand: Acquire new enterprise customers with a single platform (e.g., Network Security) and then expand the relationship by cross-selling Cloud and Security Operations platforms.
- •
Platform Consolidation: Actively target competitors' customers with compelling total cost of ownership (TCO) and security outcome advantages.
- •
M&A Integration: Drive growth by selling newly acquired capabilities (e.g., Identity Security) into the massive existing customer base.
Align sales compensation to incentivize multi-platform deals. Create dedicated 'Platform Specialist' teams to support account executives in complex cross-sell opportunities. Launch marketing campaigns focused on the theme of 'Radical Consolidation for the AI Era'.
Prioritized Initiatives
- Initiative:
CyberArk 'Synergy Sprint'
Expected Impact:High
Implementation Effort:High
Timeframe:6-12 Months
First Steps:Launch an immediate sales enablement blitz to train the entire global sales force on the CyberArk value proposition and identify the top 100 cross-sell targets in the existing customer base.
- Initiative:
Mid-Market MSSP Acceleration Program
Expected Impact:Medium
Implementation Effort:Medium
Timeframe:9 Months
First Steps:Recruit a dedicated leader for the MSSP program and launch a pilot with 10-15 key partners to co-develop the offering and commercial model.
- Initiative:
AI Security Leadership Campaign
Expected Impact:High
Implementation Effort:Medium
Timeframe:Ongoing
First Steps:Publish a seminal research report via Unit 42 on the state of AI-driven cyber threats and best practices for securing AI pipelines, establishing thought leadership in this emerging space.
Experimentation Plan
High Leverage Tests
{'test': 'Test different platform bundling and pricing models for the mid-market to find the optimal balance between features and price point.', 'hypothesis': "A simplified, all-in-one 'Business Security Platform' bundle will have a higher conversion rate than a-la-carte options for companies with <2000 employees."}
{'test': "Pilot a 'try-before-you-buy' program for Cortex XSIAM within existing Prisma Cloud customer accounts.", 'hypothesis': 'Providing a 30-day, data-ingested trial of XSIAM to cloud security customers will significantly increase qualified sales leads for the SecOps platform.'}
Utilize A/B testing platforms for digital messaging. For sales-led experiments, track metrics such as pipeline generation, conversion rate, deal size, and sales cycle length for the pilot group vs. a control group.
Monthly review of digital experiments; quarterly review of sales and strategic pilot programs.
Growth Team
A centralized Growth Strategy team that works cross-functionally with Platform GMs, Sales Operations, and Marketing. Embed 'Platform Adoption' specialists within regional sales teams.
Key Roles
- •
VP of Platform Growth: An executive responsible for the overall cross-platform strategy and hitting Platform ARR targets.
- •
Director of Competitive Intelligence & Displacement: A leader focused on creating and executing programs to win customers from key competitors.
- •
Head of MSSP & Service Provider Channel: A dedicated channel chief for the managed services route-to-market.
Invest in continuous training for the sales and marketing teams on value selling and articulating the financial (TCO/ROI) and operational benefits of a consolidated security platform.
Palo Alto Networks is in an exceptionally strong position to accelerate its growth and solidify its market leadership. Its growth foundation is robust, characterized by strong product-market fit, excellent market timing, and a highly scalable business model that consistently delivers a world-class combination of growth and profitability. The company's primary growth engine is its 'platformization' strategy, which aligns perfectly with the dominant market trend of vendor consolidation. This strategy not only drives new customer acquisition but, more importantly, creates significant expansion revenue and high switching costs, as evidenced by its rapidly growing Next-Generation Security ARR and massive Remaining Performance Obligation.
The recent, transformative acquisition of CyberArk for $25 billion is a strategic masterstroke. It addresses the most critical emerging threat vector—identity—and positions Palo Alto Networks as the only vendor capable of delivering a truly integrated, identity-aware security platform for the AI era. This move preempts competitors and creates a formidable barrier to entry. The primary challenge and immediate priority is execution: the successful integration of CyberArk's technology and teams will be the single most important factor in realizing the immense strategic and financial value of this acquisition.
Key growth opportunities lie in three areas: 1) Driving massive cross-sell of identity security into the installed base, 2) Expanding into the underserved mid-market through a dedicated MSSP channel strategy, and 3) Establishing thought and market leadership in the nascent but critical field of securing enterprise AI deployments. Overcoming the inherent complexities of its vast portfolio by delivering a seamless, unified customer experience will be critical. The recommended growth strategy is to double down on the platform narrative, making 'Radical Consolidation for the AI Era' the central theme and focusing the entire organization on driving Platform ARR as the North Star Metric.
Legal Compliance
Palo Alto Networks maintains a comprehensive and easily accessible 'Privacy Statement'. It is linked prominently in the website footer and at points of data collection, such as newsletter sign-ups. The policy is well-structured, detailing the types of information collected, purposes of use, and data sharing practices. It explicitly mentions compliance with the EU-U.S. Data Privacy Framework, the UK Extension, and the Swiss-U.S. Data Privacy Framework, demonstrating a commitment to lawful international data transfers. The company provides dedicated Privacy Datasheets for its products, which is a best-practice that enhances transparency for customers assessing their own compliance posture. The statement addresses data subject rights and provides clear mechanisms for users to manage their preferences, aligning with the principles of major regulations like GDPR. The existence of a Transparency Report on government data requests further bolsters customer trust.
The 'Terms of Use' are accessible from the website footer. The terms are comprehensive, covering aspects such as intellectual property rights, user contributions, account security, and disclaimers of liability. The language is standard for a large enterprise, establishing clear rules for website use. Notably, it specifies that the site is controlled from California, USA, and includes provisions related to use by the U.S. Government, which is relevant given their significant public sector business. For customers, the legal framework is more complex, involving a hierarchy of agreements like the End User License Agreement (EULA) and End User Support Agreement (EUSA), which are referenced and incorporated into service contracts. This multi-layered approach is standard for B2B tech companies and provides legal clarity for different engagement levels.
The provided website text does not include the content of a cookie consent banner, which is a limitation in this analysis. However, as a global company subject to GDPR, it is expected that a geographically-aware consent mechanism is in place. The Privacy Statement confirms the use of cookies and similar technologies in partnership with third-party ad networks for analytics, reporting, and targeted advertising. A key strength is the clear link to a 'Cookie Notice' for more detailed information. The website footer also includes a 'Do Not Sell or Share My Personal Information' link, which is a critical component for CCPA/CPRA compliance related to tracking technologies. The analysis assumes a robust, granular cookie consent banner is presented to users in relevant jurisdictions (e.g., the EU) allowing them to opt-in or opt-out of non-essential cookie categories.
Palo Alto Networks demonstrates a very strong data protection posture, which is a core component of its brand identity as a cybersecurity leader. Compliance with GDPR and CCPA/CPRA is explicitly addressed. GDPR alignment is shown through their adherence to the Data Privacy Framework for EU-US data transfers and the availability of a Customer Data Processing Addendum (DPA). CCPA/CPRA compliance is evident from the 'Do Not Sell or Share My Personal Information' link in the footer. The company's business model, which involves processing customer data for security purposes, necessitates a robust framework. Their privacy policy outlines a legitimate interest basis for processing personal data for network and information security, which is a key legal justification under GDPR. The provision of detailed product-specific Privacy Datasheets is a significant strength, allowing enterprise customers to conduct their own Data Transfer Impact Assessments.
The provided website text does not contain an 'Accessibility Statement' link in the main footer, representing a potential compliance gap. However, further investigation reveals that Palo Alto Networks does provide Voluntary Product Accessibility Templates (VPATs) upon request, which assess products against Section 508 and Web Content Accessibility Guidelines (WCAG) standards. This indicates an awareness and a formal process for accessibility compliance, particularly for its products sold to government entities. The lack of a public-facing, easily discoverable accessibility statement for the main marketing website is a weakness. Such a statement is a best practice to demonstrate commitment to inclusivity and mitigate legal risk under laws like the Americans with Disabilities Act (ADA).
As a leading cybersecurity provider to both public and private sectors, Palo Alto Networks' legal positioning is heavily reliant on industry-specific and governmental compliance. The website highlights a 'Product Certifications' page and a 'Trust Center', which are crucial assets for B2B and B2G (Business-to-Government) sales. They hold numerous critical certifications, including FedRAMP (for U.S. Federal Government business) , SOC 2+, ISO certifications, and standards for specific countries like Germany (C5) and Australia (IRAP). Their ability to meet stringent compliance frameworks like HIPAA, PCI DSS, and GDPR for their customers is a core part of their value proposition. They are listed on numerous government procurement contracts (GSA, NASA SEWP V), underscoring their deep integration and compliance with public sector requirements. Furthermore, as a publicly traded company, they are subject to SEC regulations regarding the disclosure of cybersecurity incidents and risk management strategies.
Compliance Gaps
- •
Lack of a prominently displayed and easily accessible 'Accessibility Statement' on the main website.
- •
The cookie consent mechanism's specifics (e.g., granularity of choice, default settings) could not be verified from the provided text, representing a potential area of risk if not implemented according to strict GDPR 'opt-in' standards.
- •
Absence of explicit information on how the company's AI-powered products address emerging AI-specific regulations and ethical guidelines.
Compliance Strengths
- •
Comprehensive and transparent Privacy Statement with clear explanations of data processing activities.
- •
Dedicated product-specific Privacy Datasheets, which aid customers in their own compliance efforts.
- •
Clear compliance with CCPA/CPRA demonstrated by the 'Do Not Sell or Share My Personal Information' link.
- •
Robust framework for international data transfers via the EU-U.S. Data Privacy Framework.
- •
Extensive and prominently displayed list of industry and government certifications (FedRAMP, ISO, SOC 2+), which is a significant competitive advantage.
- •
Presence of a 'Report a Vulnerability' program, demonstrating a commitment to security best practices.
- •
Clear and accessible links to foundational legal documents like 'Terms of Use' and 'Privacy Statement' in the website footer.
Risk Assessment
- Risk Area:
Website Accessibility
Severity:Medium
Recommendation:Publish a public-facing Accessibility Statement that affirms commitment to WCAG 2.1 AA standards. Ensure the statement provides a contact method for users with disabilities to report issues. Conduct and maintain regular accessibility audits of the marketing website.
- Risk Area:
Cookie Consent
Severity:High
Recommendation:Ensure the cookie consent banner presented to users in the EU/UK enforces a strict 'opt-in' policy for all non-essential cookies, with no pre-ticked boxes. The banner must provide granular choices and be as easy to reject as it is to accept. Maintain detailed records of user consent.
- Risk Area:
AI Regulation Compliance
Severity:Low
Recommendation:Proactively develop and publish documentation (e.g., white papers, trust center articles) detailing how Palo Alto Networks' AI-powered solutions align with emerging AI principles and regulations, such as the EU AI Act. This will build trust and provide a competitive advantage.
High Priority Recommendations
- •
Immediately ensure the cookie consent mechanism is fully compliant with GDPR's strict 'opt-in' requirements for EU/UK visitors to mitigate the high risk of regulatory fines.
- •
Create and prominently link an Accessibility Statement in the website footer to affirm commitment to WCAG standards and reduce legal risk under the ADA.
- •
Review and update data processing agreements (DPAs) to explicitly address the processing of data by AI systems, ensuring transparency and alignment with customer expectations and forthcoming regulations.
Palo Alto Networks demonstrates a sophisticated and mature legal compliance posture that is a strategic asset, not merely a defensive necessity. For a global cybersecurity leader, trust is the ultimate currency, and their legal framework is foundational to building and maintaining that trust. Their proactive and transparent approach to data privacy, evidenced by detailed product datasheets and adherence to international transfer frameworks, directly enables market access in highly regulated regions like the EU. The company's extensive list of government and industry certifications (FedRAMP, SOC 2, ISO) serves as a powerful competitive advantage, unlocking lucrative public sector and enterprise markets where compliance is a non-negotiable prerequisite. This deep investment in compliance streamlines the procurement process for customers in regulated industries like finance, healthcare, and government. While the overall legal positioning is exceptionally strong, there are minor gaps. The most notable is the lack of a prominent website accessibility statement, which is inconsistent with their otherwise comprehensive approach to corporate responsibility and risk management. Addressing this, along with ensuring their cookie consent mechanism is impeccably aligned with stringent GDPR standards, would further solidify their position as a market leader whose internal practices reflect the security and integrity they sell.
Visual
Design System
Corporate & Tech-Forward
Excellent
Advanced
User Experience
Navigation
Horizontal Mega Menu
Intuitive
Good
Information Architecture
Logical
Clear
Moderate
Conversion Elements
- Element:
Hero Section 'Get started' CTA
Prominence:Medium
Effectiveness:Somewhat effective
Improvement:Increase the visual weight and color contrast of the primary 'Get started' button. The secondary 'Sign up' CTA has a similar visual hierarchy, which can cause momentary hesitation.
- Element:
Newsletter Signup ('Get the latest news')
Prominence:Medium
Effectiveness:Effective
Improvement:The placement in the pre-footer is standard and effective. Consider adding a more compelling value proposition beyond just 'news, invites, and threat alerts' to increase sign-ups, such as 'Get exclusive threat intelligence from Unit 42'.
- Element:
'Load More' Button (Threat Research Page)
Prominence:Low
Effectiveness:Ineffective
Improvement:Replace 'Load More' with infinite scroll or pagination. For a content-rich research hub, forcing users to repeatedly click 'Load More' creates friction and hampers content discovery.
- Element:
Solutions/Product Cards
Prominence:High
Effectiveness:Effective
Improvement:The cards are well-structured. A subtle hover effect that lifts the card or highlights a 'Learn More' link could increase engagement and click-through rates.
Assessment
Strengths
- Aspect:
Cohesive Brand Identity
Impact:High
Description:The site uses a dark theme with a consistent palette of deep grays, vibrant oranges, and greens, projecting a modern, serious, and high-tech image appropriate for a cybersecurity leader. Typography (TT Hoves) and iconography are applied uniformly, reinforcing brand trust and professionalism.
- Aspect:
Clear Information Architecture for Experts
Impact:High
Description:The complex portfolio of products, services, and threat intelligence is logically organized under clear top-level navigation items like 'Products and Services', 'Solutions', and 'Resources'. This structure caters effectively to their target audience of knowledgeable enterprise IT and security professionals.
- Aspect:
High-Quality Visual Storytelling
Impact:Medium
Description:The use of abstract, data-driven visualizations and schematics effectively communicates complex technological concepts without resorting to generic stock photos. This approach enhances credibility and speaks the language of their technical audience.
Weaknesses
- Aspect:
Inconsistent CTA Hierarchy
Impact:Medium
Description:On the homepage hero, the primary and secondary CTAs ('Get started' and 'Sign up') have nearly identical visual weight. This lack of clear hierarchy can lead to decision paralysis and potentially lower conversion rates on the primary action.
- Aspect:
Moderate Cognitive Load
Impact:Medium
Description:The sheer volume of information, particularly in the mega menus and footer, can be overwhelming for first-time visitors or those less familiar with cybersecurity. While logical, the density of links requires significant user focus to parse.
- Aspect:
Passive Content Discovery
Impact:Low
Description:The 'Load More' button on the Threat Research page is an outdated UX pattern. It creates unnecessary clicks and friction for users who are actively trying to consume a large amount of valuable content, hindering deep engagement with their thought leadership.
Priority Recommendations
- Recommendation:
Establish a clear visual hierarchy for all Call-to-Action buttons.
Effort Level:Low
Impact Potential:High
Rationale:Differentiate primary, secondary, and tertiary CTAs using a consistent system of color, size, and style (e.g., solid fill for primary, ghost/outline for secondary). This will guide users to the most important actions on each page, directly impacting lead generation and user journey progression.
- Recommendation:
Implement infinite scroll or pagination on content-heavy archive pages.
Effort Level:Medium
Impact Potential:Medium
Rationale:Replacing the 'Load More' button on pages like the Cortex Cloud Security Research blog will reduce friction, increase content consumption, and improve user engagement with valuable thought leadership content, reinforcing brand authority.
- Recommendation:
Refine the mega menu design to reduce cognitive load.
Effort Level:Medium
Impact Potential:Medium
Rationale:Consider introducing subtle visual grouping (e.g., light background tints, dividers) or a two-tiered column structure within the mega menu to help users scan and process the large number of links more efficiently. This will improve findability and reduce user frustration.
Mobile Responsiveness
Good
The design appears to use a standard fluid grid system that should adapt well to different breakpoints. However, the density of information in navigation and footer elements will be the primary challenge on smaller screens.
Mobile Specific Issues
- •
The extensive mega menu will need to collapse into a well-organized accordion or multi-level flyout menu to avoid overwhelming users on mobile.
- •
Complex data visualizations and multi-column layouts on the homepage will require significant simplification or stacking to remain legible and effective on narrow viewports.
- •
Text-heavy sections may require adjustments in font size and line height to ensure optimal readability on smaller devices.
Desktop Specific Issues
On very large screens, text line lengths within content sections could become uncomfortably long, potentially harming readability. Capping the max-width of text containers would be a best practice.
Palo Alto Networks' website is a world-class example of a mature, tech-forward corporate design system. It successfully communicates its brand identity as a leading-edge, authoritative force in the cybersecurity industry. The dark-themed aesthetic is bold and professional, and the consistent application of typography, color, and iconography creates a cohesive and trustworthy experience. The information architecture is robust and logically structured to serve its primary audience: highly knowledgeable enterprise customers, government entities, and service providers. Users familiar with the cybersecurity landscape can navigate the vast portfolio of products and resources with relative ease.
The primary strengths lie in this brand consistency and the effective use of abstract, high-tech visuals for storytelling, which resonate well with a technical audience. The site successfully positions Palo Alto Networks as an innovator and thought leader, especially on pages like the 'Cortex Cloud Security Research' hub.
However, there are clear opportunities for conversion optimization and UX refinement. The most significant weakness is the inconsistent visual hierarchy among call-to-action elements. Primary and secondary CTAs often share the same visual weight, which can dilute their impact and confuse the user's journey. Additionally, while the information is well-organized, its sheer density creates a moderate cognitive load, particularly in the expansive mega menus. Outdated UX patterns, such as the 'Load More' button for discovering content, create unnecessary friction and hinder deeper engagement.
Key recommendations focus on low-effort, high-impact changes. A strategic imperative is to create and enforce a strict visual hierarchy for CTAs to guide users more effectively towards conversion goals. Secondly, modernizing content discovery patterns by replacing 'Load More' buttons will enhance user experience and increase time on site. Finally, subtle refinements to the information architecture, such as better visual grouping within mega menus, can significantly reduce cognitive load and improve usability for all user segments.
Discoverability
Market Visibility Assessment
Palo Alto Networks (PANW) has established itself as a dominant force in the cybersecurity market, widely recognized as a market leader with significant brand authority. This is strongly evidenced by its consistent placement as a 'Leader' in numerous Gartner Magic Quadrant and Forrester Wave reports, which are prominently featured on their website. Their authority is further amplified by their world-renowned threat intelligence group, Unit 42, which provides cutting-edge research, incident response, and cybersecurity consulting. This research arm functions as a powerful content engine, generating high-authority articles on emerging threats, threat actor groups, and vulnerabilities, positioning PANW not just as a vendor, but as a foundational source of industry intelligence.
Palo Alto Networks commands significant market share visibility, competing directly with other industry giants like Fortinet, Cisco, CrowdStrike, and Zscaler. While precise digital market share metrics are difficult to ascertain without internal data, PANW's strategy of 'platformization'—consolidating multiple security functions into integrated platforms like Strata, Prisma, and Cortex—is a direct and visible attempt to capture a larger share of enterprise security budgets. The recent, high-profile agreement to acquire CyberArk, a leader in identity security, is a strategic move that dramatically increases their visibility and competitive standing in the critical identity security market, directly challenging competitors by creating a more comprehensive, end-to-end platform.
The digital presence of Palo Alto Networks is strategically engineered for high-value B2B customer acquisition. The website effectively targets senior-level decision-makers (C-Suite, executives) and technical practitioners with a mix of high-level strategic content ('Perspectives' magazine, C-suite guides) and deep technical documentation and research from Unit 42. Calls-to-action are tailored to the enterprise sales cycle, including 'Demos and trials,' 'Plan a collaborative discussion' at their Executive Briefing Center, and an urgent 'Under Attack? We’re Here' link to their Unit 42 incident response team. This multi-pronged approach allows them to capture leads at all stages of the buyer's journey, from initial research to emergency response, indicating a very high potential for customer acquisition through digital channels.
Palo Alto Networks demonstrates a strong global digital presence, with website sections for worldwide events, global locations, and a partner portal catering to an international community. The availability of content and support in multiple languages (evidenced by video caption options) suggests a mature strategy for geographic market penetration. Their digital strategy appears well-equipped to engage and acquire customers from major markets across North America, Europe, and Asia-Pacific, reflecting their status as a global cybersecurity leader.
The company's digital content exhibits exceptionally broad and deep coverage of critical cybersecurity topics. From core offerings like Next-Generation Firewalls and SASE to emerging frontiers like AI Security, Cloud-Native Application Protection Platforms (CNAPP), and Extended Detection and Response (XDR), their expertise is well-documented. The Unit 42 research portal provides an extensive library of threat intelligence on ransomware, nation-state actors, and specific vulnerabilities, establishing PANW as an authority across the entire threat landscape. This comprehensive coverage ensures they are visible for a vast array of high-intent search queries, attracting a wide range of potential customers with diverse security needs.
Strategic Content Positioning
Content is well-aligned with the B2B customer journey. Awareness is driven by Unit 42's threat research, blog articles, and the 'Cyberpedia'. Consideration and evaluation are supported by detailed platform pages, solution guides, customer testimonials, and analyst reports that validate their leadership. The decision stage is facilitated by clear calls-to-action for demos, executive briefings, and direct contact with the sales or incident response teams. This structured approach effectively nurtures prospects from initial problem identification to final purchase.
Palo Alto Networks already excels at thought leadership through Unit 42. The primary opportunity is to build a dominant narrative around the convergence of AI and security. By heavily promoting their 'Precision AI' framework and the strategic rationale behind the CyberArk acquisition (securing human and machine identities in the AI era), they can position themselves as the definitive visionary for securing the AI-driven enterprise. Creating more C-suite accessible content that translates their deep technical research into strategic business risk and resilience conversations is a key opportunity.
While PANW's technical content is top-tier, competitors like CrowdStrike have been effective at creating relatable, human-centric marketing narratives and deep educational content for very broad, top-of-funnel keywords. PANW could benefit from developing more content that simplifies complex topics for non-technical executives, focusing on business outcomes (e.g., cost reduction from platform consolidation, risk mitigation in financial terms). There is also an opportunity to create more interactive tools, like AI readiness assessments or industry-specific risk calculators, to engage potential customers earlier in their journey.
Brand messaging is exceptionally consistent and disciplined across the digital presence. The core strategic pillars of 'Platformization' and 'AI-powered security' (specifically 'Precision AI') are woven throughout the homepage, product pages, and strategic announcements. The recent announcement to acquire CyberArk is framed perfectly within this narrative, presenting it as the next logical step to create 'the end-to-end security platform for the AI era.' This consistency reinforces their market position and strategic direction effectively.
Digital Market Strategy
Market Expansion Opportunities
- •
Dominate the 'Identity Security' narrative by leveraging the CyberArk acquisition to create a comprehensive content hub focused on securing identities in the age of AI, targeting CISOs and CIOs.
- •
Develop dedicated, solution-oriented content hubs for key industry verticals (e.g., Finance, Healthcare, Manufacturing) that package platform benefits and case studies to address specific compliance and threat model challenges.
- •
Expand into the emerging 'AI Security Posture Management' (AI-SPM) market through content that highlights the capabilities gained from the Protect AI acquisition and the new Prisma AIRS platform.
Customer Acquisition Optimization
- •
Create high-intent, problem-focused campaigns targeting long-tail keywords around reducing security tool complexity and lowering TCO through platform consolidation.
- •
Prominently feature the Unit 42 'Under Attack?' incident response service in paid search and social campaigns during major industry breach announcements to capture high-urgency leads.
- •
Develop account-based marketing (ABM) content streams tailored to key enterprise accounts, using data from their digital engagement to personalize outreach and executive briefing invitations.
Brand Authority Initiatives
- •
Launch a major thought leadership campaign co-branded with CyberArk post-acquisition, featuring joint research and a unified vision for identity-first security.
- •
Produce a flagship annual 'State of AI Security' report from Unit 42, establishing a benchmark for the industry and generating significant media citations.
- •
Host exclusive, high-level virtual summits for C-suite executives that translate the findings of their technical threat research into strategic business implications and board-level conversations.
Competitive Positioning Improvements
- •
Sharpen messaging to explicitly contrast the benefits of an integrated, AI-powered platform against the complexity and security gaps of using multiple point solutions from competitors.
- •
Launch a competitive displacement campaign focused on the TCO and operational efficiency gains of their platform, targeting customers of key competitors like Fortinet and CrowdStrike.
- •
Frame their AI capabilities ('Precision AI') as a core differentiator that delivers superior, automated threat detection and response compared to competitors' less integrated AI features.
Business Impact Assessment
Market share is best indicated by 'share of voice' in key growth categories like SASE, XDR, and Cloud Security. Continued leadership in analyst reports (Gartner, Forrester) serves as a primary benchmark. Growth in Next-Generation Security (NGS) Annual Recurring Revenue (ARR) is the key financial metric reflecting the success of their platformization strategy in capturing a larger share of customer wallet.
Key metrics include the number of qualified leads generated from high-value content (e.g., Unit 42 reports), demo requests for their core platforms, and bookings for the Executive Briefing Center. A critical metric is the number of incident response engagements initiated through the website, as these often lead to larger platform deals.
Authority can be measured by the volume of media mentions and citations of Unit 42 research, branded search volume, and social media engagement with their thought leadership content. Inbound links from reputable industry and news sites to their research serve as a strong indicator of authority and trust.
Success should be benchmarked by tracking search engine rankings for strategic, non-branded keywords (e.g., 'SASE solution,' 'AI powered SOC') against primary competitors like Fortinet and CrowdStrike. Analyzing competitor messaging around platform and AI strategies is crucial to ensure PANW's narrative remains differentiated and superior.
Strategic Recommendations
High Impact Initiatives
- Initiative:
Launch the 'Identity-First Security for the AI Era' Campaign
Business Impact:High
Market Opportunity:Capitalize on the CyberArk acquisition to become the undisputed thought leader in the convergence of identity security and AI. This addresses a primary vector for modern breaches.
Success Metrics
- •
Organic search ranking for 'identity security' and related terms
- •
Lead generation from identity security content
- •
Media citations of the joint PANW-CyberArk vision
- Initiative:
Develop Industry-Specific Platformization Blueprints
Business Impact:High
Market Opportunity:Address the unique security and compliance needs of high-value verticals like finance and healthcare, moving beyond a horizontal technology pitch to a tailored business solution.
Success Metrics
- •
Engagement with industry-specific content hubs
- •
Number of demo requests from target verticals
- •
Increase in multi-platform deals within those industries
- Initiative:
Establish the Unit 42 Annual 'AI Threat Report' as the Industry Gold Standard
Business Impact:Medium
Market Opportunity:Solidify PANW's position as the leading authority on AI-driven threats and defense, attracting top-of-funnel interest and generating unparalleled brand credibility.
Success Metrics
- •
Number of report downloads
- •
Volume of media and analyst citations
- •
Inbound links to the report page
The overarching strategy is to aggressively position Palo Alto Networks as the essential, unified security platform for the AI era. This involves shifting the market conversation from buying disparate 'best-of-breed' point products to adopting a single, integrated platform that reduces complexity, lowers total cost of ownership, and provides superior security outcomes through the power of data and AI. The CyberArk acquisition must be positioned as the critical final piece in this platform, making identity the new security perimeter.
Competitive Advantage Opportunities
- •
The unparalleled breadth of the integrated platform, now including market-leading identity security, which competitors cannot easily replicate.
- •
The world-class, proprietary threat intelligence from Unit 42, which fuels both product efficacy and marketing authority.
- •
A clear and committed 'AI-first' vision ('Precision AI') that is demonstrably integrated across the entire platform, positioning them as more innovative and future-proof than competitors.
Palo Alto Networks has cultivated a formidable digital market presence that effectively projects its status as a global cybersecurity leader. The company's strategy is built on two powerful pillars: the unparalleled brand authority of its Unit 42 threat intelligence group and a disciplined, consistent brand message centered on 'platformization' and AI-powered security.
The website functions as a highly effective B2B customer acquisition engine, seamlessly guiding distinct personas—from C-suite executives to hands-on security practitioners—through a well-structured content journey. High-value assets like Unit 42's in-depth research and prominent placements in key analyst reports serve as powerful validation, driving consideration and trust.
The recent announcement of the agreement to acquire CyberArk is a pivotal strategic inflection point. This move is not merely an addition; it is the capstone of their platformization strategy, positioning Palo Alto Networks to dominate the crucial conversation around identity as the new security perimeter, especially in the context of AI. This creates a significant competitive advantage that rivals with less comprehensive portfolios will struggle to counter.
Strategic recommendations should focus on fully capitalizing on this acquisition. The highest impact initiative will be to launch a massive thought leadership campaign that defines the future of 'Identity-First Security' in the AI era, cementing their position as the visionary leader. Secondly, they must translate their platform's technical superiority into tangible business outcomes for specific, high-value industry verticals, creating tailored digital experiences that speak directly to industry-specific challenges. Finally, continuing to elevate the Unit 42 brand as the definitive source on emerging threats, particularly those involving AI, will protect their core source of market authority and top-of-funnel lead generation. By executing on these strategic fronts, Palo Alto Networks can leverage its digital presence to accelerate market share capture and solidify its position as the indispensable security partner for the modern enterprise.
Strategic Priorities
Strategic Priorities
- Title:
Execute 'Project Apex': Drive Identity-First Security Dominance via CyberArk Integration
Business Rationale:The $25B CyberArk acquisition is the company's most significant strategic bet, aimed at creating an unassailable end-to-end security platform. Flawless and rapid integration is critical to realize massive cross-sell synergies, redefine the market around identity-aware security, and preempt competitors from closing this strategic gap.
Strategic Impact:This transforms Palo Alto Networks from a leading security platform vendor into the category-defining 'digital immune system' for the AI era, with identity as the central nervous system. It creates a powerful competitive moat that rivals built on network or endpoint security cannot easily replicate.
Success Metrics
- •
CyberArk Cross-Sell ARR into PANW customer base
- •
Percentage of Fortune 500 customers with integrated PANW + CyberArk solutions
- •
Time-to-market for first deeply integrated platform feature (e.g., Identity Threat Detection in Cortex XSIAM)
Priority Level:HIGH
Timeline:Strategic Initiative (3-12 months)
Category:Market Position
- Title:
Launch 'Radical Consolidation' Program to Prove Platform Value
Business Rationale:The core 'platformization' strategy is sound, but customers require a compelling financial and operational justification to displace entrenched point solutions. A formal, data-driven program is needed to articulate superior Total Cost of Ownership (TCO), reduced complexity, and improved security outcomes, accelerating migrations and capturing competitor wallet share.
Strategic Impact:Shifts the primary sales motion from product features to strategic business value (cost savings, risk reduction, operational efficiency). This creates a scalable, repeatable engine to convert competitor customers and significantly deepen the footprint within the existing customer base.
Success Metrics
- •
Platform ARR (revenue from customers with 3+ platform modules)
- •
Competitive Displacement Win Rate (%) against key rivals
- •
Increase in average deal size for multi-platform contracts
Priority Level:HIGH
Timeline:Strategic Initiative (3-12 months)
Category:Customer Strategy
- Title:
Establish Definitive Leadership in the 'AI Security' Category
Business Rationale:With every enterprise rushing to adopt AI, securing AI models, data, and infrastructure is the next major cybersecurity frontier. By leveraging Unit 42's research and the Prisma platform, the company can move beyond defending against AI threats to becoming the essential partner for enabling secure AI adoption, a far more strategic and valuable market position.
Strategic Impact:Positions Palo Alto Networks as the visionary leader in the decade's most important technology shift, attracting premium customers and top talent. It enables the creation of a new high-growth product category (e.g., AI Security Posture Management) that the company can define and dominate.
Success Metrics
- •
Market share in the emerging AI Security category
- •
Revenue from AI Security-specific products/modules
- •
Volume of media and analyst citations of Unit 42's 'State of AI Security' research
Priority Level:HIGH
Timeline:Strategic Initiative (3-12 months)
Category:Brand Strategy
- Title:
Formulate and Launch a Dedicated Mid-Market Penetration Strategy
Business Rationale:The current enterprise-focused Go-To-Market model and premium pricing create a barrier to the large, fast-growing mid-market segment, ceding ground to competitors like Fortinet. A dedicated strategy with tailored product bundles, simplified pricing, and a channel-first (MSSP) approach is required to unlock a new multi-billion dollar revenue stream.
Strategic Impact:Significantly expands the Total Addressable Market (TAM) and diversifies the customer base beyond the large enterprise. This creates a new, durable engine for sustained, long-term growth and insulates the business from enterprise spending cycles.
Success Metrics
- •
Mid-Market Segment Revenue Growth (%)
- •
Number of active, revenue-generating MSSP partners
- •
New logo acquisition velocity in the mid-market segment
Priority Level:HIGH
Timeline:Strategic Initiative (3-12 months)
Category:Market Position
- Title:
Transform the Global Partner Ecosystem for Full-Platform Sales and Delivery
Business Rationale:The company's traditional channel is skilled at selling network firewalls but is less equipped to sell and service complex, multi-platform cloud (Prisma) and SOC (Cortex) solutions. A strategic overhaul of the partner program—focusing on deep technical enablement, service delivery certification, and incentives for multi-platform sales—is critical to scale the platform strategy globally.
Strategic Impact:Creates a global force multiplier for the direct sales team, accelerating the adoption of the highest-growth platforms. It also builds a certified delivery ecosystem, ensuring customer success and long-term value realization from the full platform investment.
Success Metrics
- •
Percentage of Channel Revenue from Prisma and Cortex platforms
- •
Growth in partner-led professional services bookings
- •
Number of partners with advanced certifications in all three core platforms
Priority Level:HIGH
Timeline:Long-term Vision (12+ months)
Category:Partnerships
Palo Alto Networks must cement its position as the indispensable security platform for the AI era. The immediate imperative is flawlessly integrating CyberArk to make identity the core of the platform, while simultaneously launching a value-centric go-to-market motion to accelerate enterprise-wide consolidation and capture the next frontier of AI security.
The key competitive advantage is being the only provider of a truly comprehensive, integrated security platform spanning network, cloud, SOC, and now market-leading identity security, all fueled by elite, AI-driven threat intelligence.
The primary growth catalyst will be the aggressive cross-selling of the newly acquired CyberArk identity security solutions into Palo Alto Networks' massive installed base, which includes 95% of the Fortune 100, unlocking immense and immediate revenue synergies.